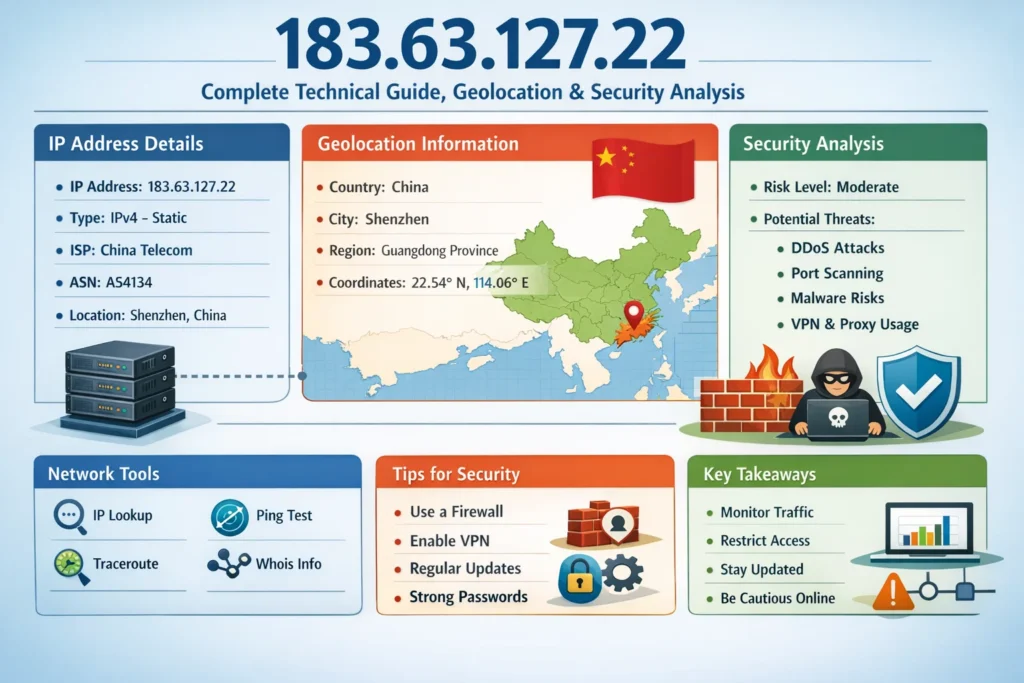
The IP address 183.63.127.22 represents far more than a random string of numbers. In today’s digital ecosystem, every public IPv4 address plays a measurable role in internet infrastructure, cybersecurity monitoring, web analytics, traffic routing, and network management. Understanding how an IP like 183.63.127.22 functions within global networks can reveal valuable insights about geolocation, ISP routing, potential security implications, and data flow patterns.
Public IP addresses are essential components of internet communication. They enable devices to send and receive data across interconnected systems worldwide. Whether the context involves cybersecurity investigation, SEO traffic analysis, server monitoring, or firewall configuration, a single IP address can hold significant informational value. This in-depth guide explores technical structure, ownership classification, geolocation, cybersecurity relevance, and practical use cases while maintaining clarity and readability for both beginners and professionals.
Understanding the Structure of IPv4 Addresses
An IPv4 address consists of four octets separated by periods. Each octet ranges from 0 to 255, forming a 32-bit numerical identifier. This structure allows for approximately 4.3 billion unique addresses globally. The address format follows a hierarchical system designed to simplify routing and identification.
The address 183.63.127.22 falls within the public IPv4 space. Public addresses are globally routable, meaning they can be accessed across the internet. They differ from private IP ranges such as 192.168.x.x or 10.x.x.x, which are reserved for internal networks. When analyzing any IP, understanding whether it belongs to public, private, or reserved ranges is the first step in determining its role within network architecture.
IPv4 exhaustion has increased the importance of efficient IP allocation. Regional Internet Registries allocate blocks of addresses to internet service providers, who then distribute them to customers. This hierarchical allocation system ensures structured global routing.
Geolocation and Regional Allocation Insights
Geolocation databases typically associate IP blocks with a specific country and sometimes a city. The IP range containing 183.63.127.22 is commonly linked to mainland China based on registry allocation data. However, IP geolocation is not always exact. It identifies the ISP’s registered location rather than the precise device location.
Geolocation plays a crucial role in cybersecurity, digital marketing, and compliance. Businesses use it to apply geo-restrictions, detect unusual login activity, and analyze website visitor patterns. If a website primarily serves users in South Asia but receives significant traffic from East Asia tied to addresses like 183.63.127.22, administrators may evaluate whether traffic is legitimate or automated.
IP geolocation databases are updated regularly, but they can vary slightly depending on the provider. Professional cybersecurity analysts often cross-reference multiple databases before drawing conclusions.
ISP and Network Ownership Analysis
Each public IP block is assigned to an Internet Service Provider. The 183.x.x.x range is generally associated with Chinese telecommunications infrastructure. Large providers manage millions of addresses and distribute them dynamically to residential and business customers.
Dynamic IP assignment means the address can change periodically. If 183.63.127.22 is assigned dynamically, it may represent different users over time. Static IP assignments, in contrast, remain fixed and are typically used by businesses, hosting providers, or enterprise servers.
ISP-level analysis helps determine whether an IP is residential, corporate, data center-based, or mobile network-based. This classification influences how cybersecurity systems evaluate risk. Residential IPs are often treated differently than hosting provider IPs in fraud detection algorithms.
Technical Breakdown Table of 183.63.127.22
The following table provides structured insights into the IP classification and related network attributes:
| Attribute | Details |
|---|---|
| IP Version | IPv4 |
| Public or Private | Public |
| Allocation Region | Asia |
| Likely Country | China |
| Address Type | Typically Dynamic (ISP Assigned) |
| Routing | Globally Routable |
| Reverse DNS | Dependent on ISP Configuration |
| Risk Assessment | Context-Based (Traffic Dependent) |
This table simplifies high-level analysis while acknowledging that real-time verification may change details depending on current ISP allocation.
Reverse DNS and Hostname Investigation
Reverse DNS lookup converts an IP address into a hostname. Not all IPs have reverse DNS entries. When configured, the hostname may reveal ISP branding or routing information.
For example, a reverse DNS record might contain telecom-related naming patterns, identifying infrastructure routing paths. If 183.63.127.22 has an active reverse DNS entry, it may display a structured domain reflecting regional infrastructure. If no record exists, that does not automatically indicate malicious intent; many dynamic addresses lack configured PTR records.
Reverse DNS is frequently used in email security. Mail servers often verify that the sending IP has a valid reverse DNS entry to reduce spam risk.
Cybersecurity Implications and Threat Assessment
IP addresses can appear in security logs for various reasons. An address may be associated with legitimate web browsing, automated crawlers, vulnerability scanning, or malicious activity. Without behavioral context, no IP should be labeled as harmful.
Security teams evaluate:
- Login attempts frequency
- Failed authentication patterns
- Port scanning behavior
- Bot traffic indicators
- Reputation database listings
A cybersecurity analyst once noted, “An IP address is not guilty by default; behavior defines risk.” This principle remains central to responsible threat analysis.
If 183.63.127.22 appears in firewall logs repeatedly attempting unauthorized access, further investigation is warranted. However, if it appears as normal traffic within analytics reports, it may simply represent standard user activity.
Role in Website Traffic and SEO Monitoring
IP analysis supports search engine optimization and analytics integrity. Traffic originating from unexpected regions may indicate referral spam, bot scraping, or competitor monitoring.
For website owners in Pakistan or India working on SEO growth strategies, monitoring international traffic patterns is essential. If traffic spikes occur from East Asia involving addresses like 183.63.127.22, reviewing server logs ensures data quality remains intact.
Search engines themselves use vast IP networks. Distinguishing between legitimate crawler activity and harmful automation requires log analysis and bot signature verification.
Firewall Configuration and Network Security Controls
Firewalls use IP addresses to permit or block traffic. Administrators may create rules based on geographic patterns, threat intelligence feeds, or abnormal activity thresholds.
Blocking a single IP like 183.63.127.22 may not be effective long-term if the ISP rotates addresses dynamically. Instead, rate limiting, CAPTCHA implementation, and anomaly detection offer more sustainable protection strategies.
Advanced security systems rely on behavioral modeling rather than static IP blocking. This approach prevents false positives while maintaining usability for legitimate visitors.
Commerce Advice onPressCapital: A Complete Guide to Smart Business Growth and Financial Success
IP Reputation and Blacklist Considerations
Several global databases track IP reputation. These include spam reporting systems, malware distribution trackers, and botnet intelligence platforms. Being listed on a blacklist does not permanently define an IP; listings often expire once malicious behavior ceases.
If 183.63.127.22 were to appear on a blacklist, remediation would involve ISP review and reputation clearing processes. ISPs frequently recycle addresses, meaning previous misuse by one user can affect a new user temporarily.
Maintaining clean server logs and monitoring outbound traffic reduces the risk of reputation damage for businesses managing their own IP allocations.
Data Privacy and Legal Implications
IP addresses are considered personal data in certain jurisdictions. Regulations such as GDPR treat them as identifiable information when combined with additional context.
Companies collecting IP data for analytics must disclose usage in privacy policies. Transparency builds trust and ensures regulatory compliance. Logging addresses like 183.63.127.22 for security purposes is standard practice, but retaining them indefinitely without purpose may violate privacy principles.
Responsible data handling balances security with individual rights.
Differences Between IPv4 and IPv6
While IPv4 addresses like 183.63.127.22 remain widely used, IPv6 adoption is increasing. IPv6 uses 128-bit addressing, vastly expanding available combinations.
IPv4 exhaustion has led to network address translation and shared IP scenarios. Many users may share a single public IP behind NAT systems. This reality complicates attribution and requires careful forensic analysis.
Transition strategies include dual-stack deployment and IPv6 tunneling to maintain compatibility.
Log File Analysis and Forensic Applications
Server logs record IP addresses during HTTP requests, SSH connections, and email exchanges. Reviewing logs helps detect suspicious behavior patterns.
A single occurrence of 183.63.127.22 in logs may indicate normal browsing. Hundreds of rapid POST requests could indicate automated attacks. Context determines interpretation.
Forensic investigators examine timestamps, user-agent strings, session cookies, and request types alongside IP addresses to build a complete activity profile.
Network Routing and BGP Considerations
Border Gateway Protocol governs how IP blocks are advertised across the internet. ISPs announce ownership of ranges, enabling global routing.
Misconfigurations or hijacking incidents can temporarily reroute traffic. Although rare, such events highlight the importance of route validation technologies like RPKI.
Routing stability ensures that data packets reach intended destinations without interception or delay.
Business Use Cases for IP Intelligence
IP intelligence tools support:
Fraud prevention
Ad targeting accuracy
Content localization
Compliance filtering
Server load balancing
E-commerce platforms analyze IP distribution to detect payment fraud risks. If a transaction originates from an IP block far outside the customer’s usual location, additional verification may be triggered.
Digital marketers use regional IP data to tailor campaigns. However, ethical practices require transparent data usage policies.
Hosting Providers vs Residential IPs
Hosting provider IPs often originate from data centers and are easier to classify as automated traffic. Residential IPs, assigned by ISPs, typically represent real consumer activity.
If 183.63.127.22 belongs to a residential ISP allocation, automated systems treat it differently from a known cloud hosting subnet. Risk scoring models assign weighted values accordingly.
Understanding IP classification improves decision-making in cybersecurity and analytics.
Monitoring Tools and Practical Implementation
Professionals use various tools for IP analysis:
WHOIS lookup services
Reverse DNS checkers
IP reputation databases
Firewall log analyzers
Geolocation APIs
Integrating these tools creates a layered understanding. No single database provides complete certainty; cross-referencing enhances reliability.
Consistent monitoring strengthens network defense posture while preserving accessibility for legitimate users.
Ethical Considerations in IP Tracking
Tracking IP addresses must respect legal boundaries. Over-monitoring without transparency damages user trust.
Security analyst Bruce Schneier once stated, “Security is a process, not a product.” Effective IP monitoring aligns with this philosophy, focusing on continuous improvement rather than reactive blocking.
Balancing vigilance with fairness ensures sustainable digital ecosystems.
Future Outlook of IP Addressing
IPv4 addresses like 183.63.127.22 will remain active for years despite IPv6 expansion. Transitional technologies support coexistence.
Increasing cybersecurity threats demand smarter analytics rather than simple IP bans. Artificial intelligence–driven behavioral models are reshaping how networks interpret IP-based risk.
The internet’s evolution depends on adaptive infrastructure and responsible governance.
Conclusion
IP addresses serve as foundational elements of internet communication. The address 183.63.127.22 illustrates how a single IPv4 identifier can carry layered meaning across geolocation, ISP allocation, cybersecurity monitoring, analytics, and compliance considerations. Proper analysis requires context, behavioral evaluation, and responsible interpretation rather than assumptions.
Understanding public IP structure empowers businesses, developers, marketers, and security professionals to make informed decisions. Whether reviewing logs, configuring firewalls, or analyzing SEO traffic patterns, structured IP intelligence enhances operational clarity. As internet infrastructure continues evolving, balanced and ethical IP management remains essential for long-term digital resilience.
Frequently Asked Questions
What type of IP address is 183.63.127.22?
183.63.127.22 is a public IPv4 address. Public addresses are globally routable and assigned by Internet Service Providers to users or businesses for internet communication.
Can 183.63.127.22 identify an exact physical location?
No IP address, including 183.63.127.22, provides precise physical location details. Geolocation databases typically identify country or regional ISP registration rather than a specific home or office address.
Is 183.63.127.22 dangerous or malicious?
An IP address alone is not inherently dangerous. The risk associated with 183.63.127.22 depends entirely on observed behavior such as spam, scanning, or unauthorized access attempts.
Why does 183.63.127.22 appear in my server logs?
It may appear because a device using that address accessed your website or server. Reviewing timestamps, request types, and frequency helps determine whether the activity was normal browsing or automated traffic.
Can I block 183.63.127.22 from accessing my website?
Yes, firewalls and server configurations allow IP blocking. However, if the address is dynamically assigned by an ISP, blocking it may only temporarily prevent access while potentially affecting legitimate users.